Increasingly, we are seeing phishing emails targeting students in an attempt to steal their money through a fake job scam. Historically, phishing attacks were generally trying to steal students’ accounts and personal information in order to send out other scam emails to individuals outside the university. This year, however, we have seen a shift in attackers directly targeting our students with scams. Sadly, we have also seen several students fall victim to these scams after retrieving the emails from the quarantine. Remember to be VERY cautious with any email sent to the quarantine.
What To Watch Out For
These attacks follow a common theme: they all offer a job that pays extremely well for the very small amount of work required. The work is often very general, and anyone would be qualified for it. Often, the advertised pay exceeds $100/hour which is far above the actual level of pay for these kinds of jobs.
Common Indicators
How They Will Steal Your Money
The scam will generally work as follows: The attacker sends thousands of emails to EKU students promising a too-good-to-be-true job. Scammers only need to fool a couple of students for the scam to be successful. Once you reply, they conduct a fake and usually very simple online job interview, usually via text or chat. You will then be offered the job! Then, they will send you a check to cash, which you are to use to purchase a computer and other equipment needed for the job. They will direct you to a “vendor” where you should purchase that equipment. Often, the check will be for more than the cost of the equipment, and they will tell you to keep the extra money as a “bonus.” You will buy the equipment from the vendor, which is not a real storefront and is just the attackers taking your money. The check will then bounce from your bank as it will turn out that it was a fake check, and the bank will remove that money from your account.
As a result, you are out hundreds—maybe even thousands—of dollars by purchasing equipment that you will never receive for a job that is not real. You can contact the police, but there will be little they can do to help. The attackers are almost always located in countries where US law enforcement has no ability to track them down or arrest them.
Examples
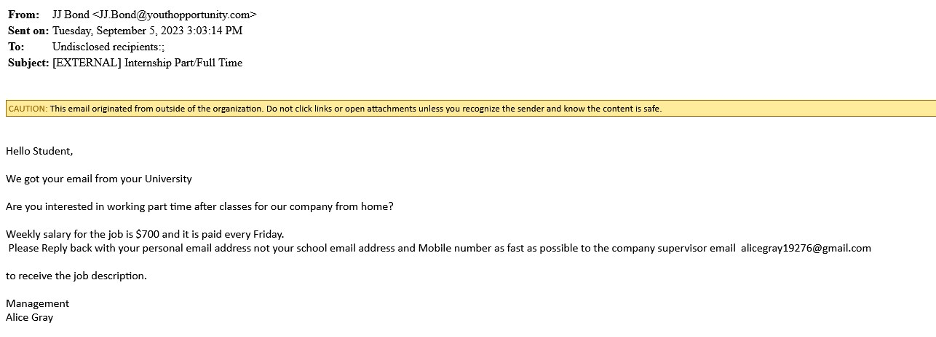
Sometimes, scams are just an email with all of the information in the body. Note that this offers a too-good-to-be-true job and requests you to change what email you are using to communicate with them.
Often, the body of the scam email is empty, but the information is in an attachment (please note that you should never open attachments from unknown senders).
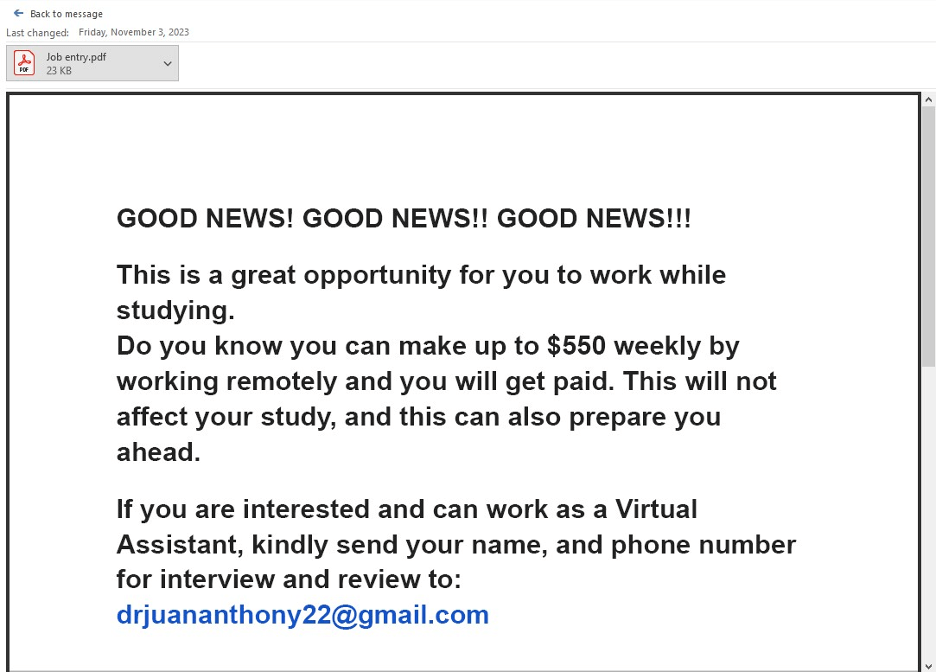
Here is an example of the contents of a scam attachment. Note that it features similar language and indicators that it is a scam to the email body above.
